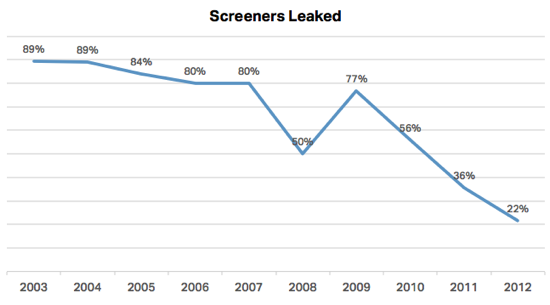
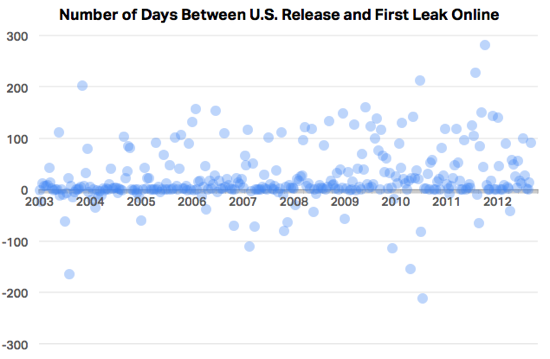
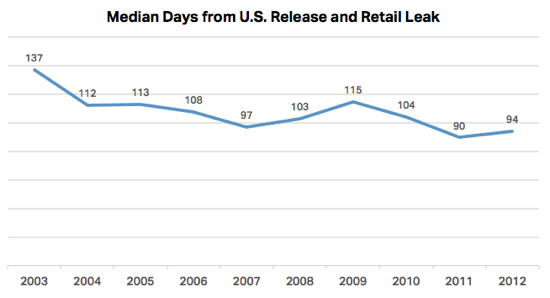
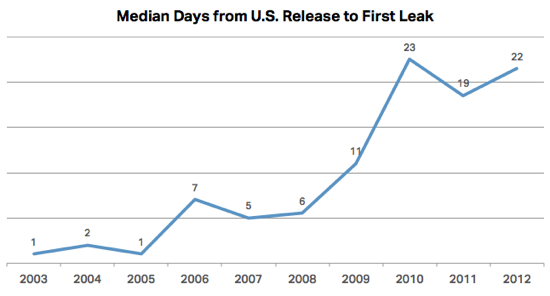
Last Friday, a YouTube user named eeplox posted a question to the support forums, regarding a copyright complaint on one of his videos. YouTube’s automated Content ID system flagged a video of him foraging a salad in a field, claiming the background music matched a composition licensed by Rumblefish, a music licensing firm in Portland, Oregon.
The only problem? There is no music in the video; only bird calls and other sounds of nature.
Naturally, he filed a dispute, explaining that the audio couldn’t possibly be copyrighted.
The next day, amazingly, his claim was rejected. Not by YouTube itself — it’s unlikely that a Google employee ever saw the claim — but from a representative at Rumblefish, who reviewed the dispute and reported back to YouTube that their impossible copyright for nonexistent music was indeed violated.
Back at YouTube, eeplox found himself at a dead end. YouTube now stated, “All content owners have reviewed your video and confirmed their claims to some or all of its content.” No further disputes were possible, the case was closed.
Whether caused by a mistake or malice, Rumblefish was granted full control over eeplox’s video. They could choose to run ads on the video, mute the audio, or remove it entirely from the web.
A History of Screw-Ups
On Sunday night, Reddit took notice. Within hours, the thread was on the homepage, commenters were freaking out and, to his credit, Rumblefish CEO Paul Anthony was fielding questions in an IAmA interview until 2:30am.
His argument: One of Rumblefish’s Content ID reps made a mistake by denying the dispute, and they released the claim on Sunday night. “We review a substantial amount of claims every day and the number is increasing significantly,” said Anthony. “We have millions of videos now using our songs as soundtracks and keeping up is getting harder and harder.”
This is the latest in a long series of foibles or outright abuses of YouTube’s Content ID system. Content ID was intended to help copyright holders manage the chaos of YouTube. They’d provide copies of their audio and video for analysis, which would then algorithmically match newly-uploaded videos. If a match was found, rightsholders could automatically block the video or, increasingly, claim money from video advertising.
Content ID’s monetization was a huge boon for copyright holders. Uploaders could keep their videos online, while copyright holders profited from the creative reuse of their work.
But the last couple years have seen a dramatic rise in Content ID abuse, using it for purposes that it was never intended. Scammers are using Content ID to steal ad revenue from YouTube video creators en masse, with some companies claiming content they don’t own, deliberately or not. The inability to understand context and parody regularly leads to “fair use” videos getting blocked, muted or monetized.
Bypassing the DMCA
The problem is that media companies and scammers are using Content ID as an end run around the DMCA.
With the DMCA, the process works like this. A rightsholder could file a claim against a video with YouTube, and YouTube would immediately take the video offline. If there was a mistake, the uploader could file a counter-notice. The video would then be restored by YouTube within 10-14 business days of the counter-notice, unless it went to court.
It wasn’t perfect, by any means, but it was fair. Disputes could always be appealed, and both parties were given equal power. And if a claimant lied about owning the copyright to the material in question, they could face perjury charges.
The current system, led by Content ID, tips the balance far in favor of the claimant.
Rumblefish never needed to prove they were the copyright holder, but were still given ultimate control over the video’s fate. Uploaders can dispute claims, but the only people reviewing claims are the Content ID partners that filed the claim in the first place, who are free to deny them wholesale.
A Simple Fix
The solution is simple: if a copyright holder wants to pursue a disputed Content ID match, they should file a DMCA claim. That’s the only way to guarantee their rights, and make the copyright holder legally responsible for telling the truth.
In fact, this is exactly how YouTube says that Content ID “fair use” claims should work. In practice, this doesn’t appear to be true any longer. Content ID partners, of course, can file a DMCA notice at any time, but why bother if they can reject the counter-claims themselves?
(Preferred partners like Universal Music Group can go a step further and block videos directly without filing a claim.)
This problem has been on YouTube’s radar for at least two years, but it’s only getting worse as unsavory companies discover this nascent business model. Claim copyright on media you may or may not own, and let Content ID do the rest.
By letting Content ID partners have the final word, and not trusting their own users, YouTube is violating its trust with its community and damaging fair use in the process.
Update
I originally published this article over at Wired, where a commenter pointed out that this process may actually violate YouTube’s “safe harbor” granted through the DMCA. If they choose to ignore disputes, they’re effectively giving content providers an end run around fair use and the DMCA.
Selfish Crab wrote:
It seems like by providing the Content ID system, Youtube was trying to pre-emptively identify copyrighted material, like a first-pass dispute system. Their lawyers probably concluded that so long as the content ID system falls back onto DMCA takedown procedure, they are still in compliance with the DMCA sufficiently to retain their safe harbor.
So if Content ID claim disputes do not fall back onto DMCA takedown, as Andy’s article suggests, there’s a case to be made that YouTube no longer has liability protection from users. It is a whole another can of worms to analyze what a legal claim against youtube would look like. You’d have to look at the YouTube Terms of Service (i.e., the contract) to see if maybe they contracted around this problem already, you’d have to figure out damages, etc etc. Or I guess you can just raise a shitstorm and that’s enough of a moral victory.
In a Google+ comment last December, senior copyright counsel for Google and former EFF staff attorney Fred von Lohmann acknowledged the problem.
Yes, we’re aware of that problem in the Content ID dispute process and are looking at what we can do to fix it. It’s the result of a complicated collision of how to handle geographically limited Content ID claims, disputes, and global DMCA removals. Turns out to be a hard problem to figure out. But we’re thinking on it.
Virginia law student Patrick McKay got in touch with Annie Baxter, a public relations manager at YouTube, about this issue.
This is one of those corner-case outcomes that emerges from several different rules, none of which was intended to yield the result you’ve encountered (i.e., DMCA takedowns are global, but Content ID ownership claims are territorial). Unfortunately, addressing it YouTube-wide is going to take some time, both for pondering and implementing.
So while we can promise you that we’re thinking about this, we can’t promise you a fix or time-table. And feel free to tell the OVC we’re looking at it and trying to come up with something.
In the meantime, anyone in the Content ID program is offered free rein to claim copyright on your videos and profit directly from them. I’m hoping this gets cleared up soon.